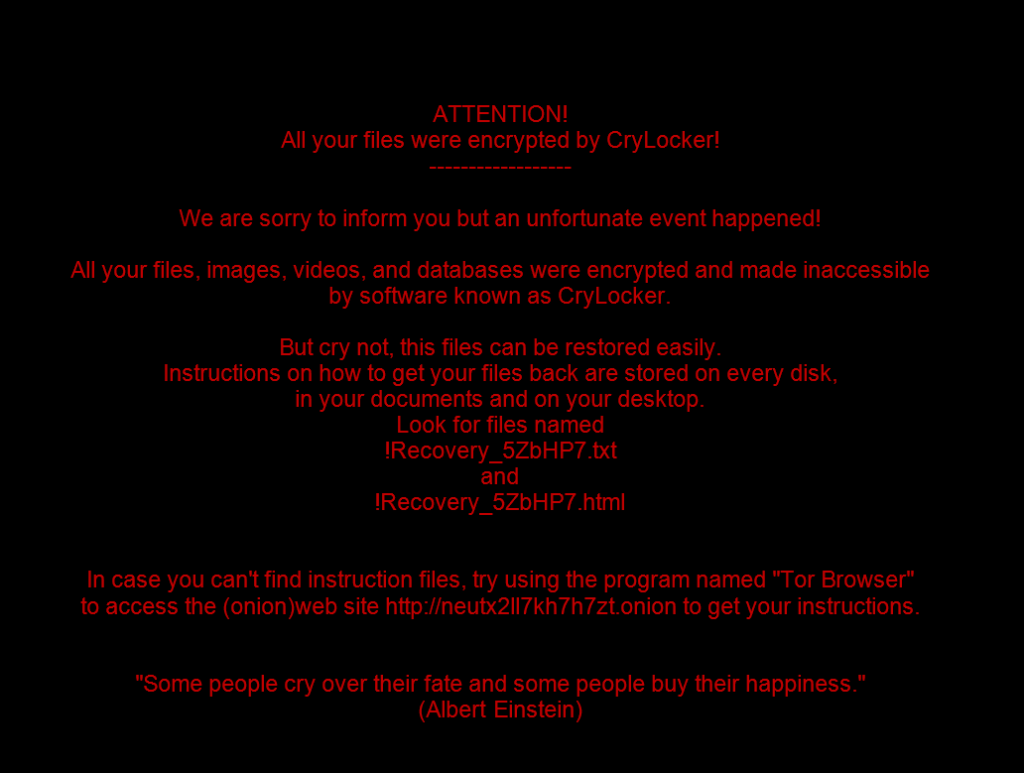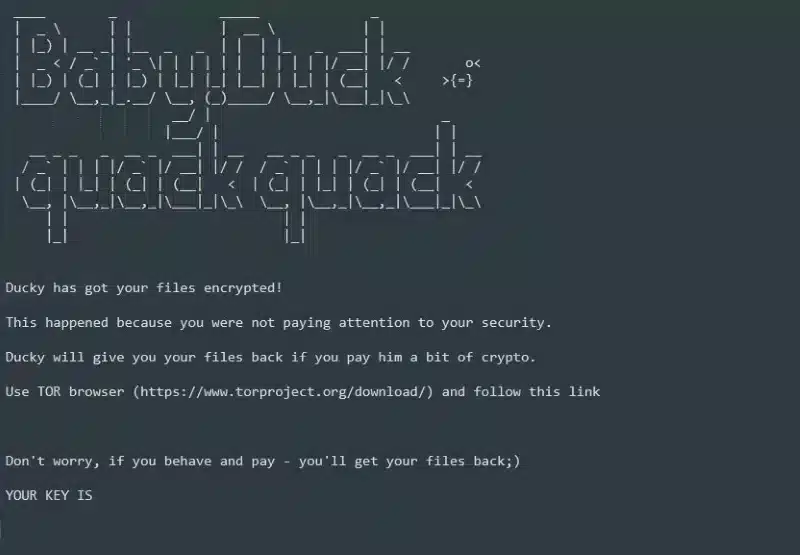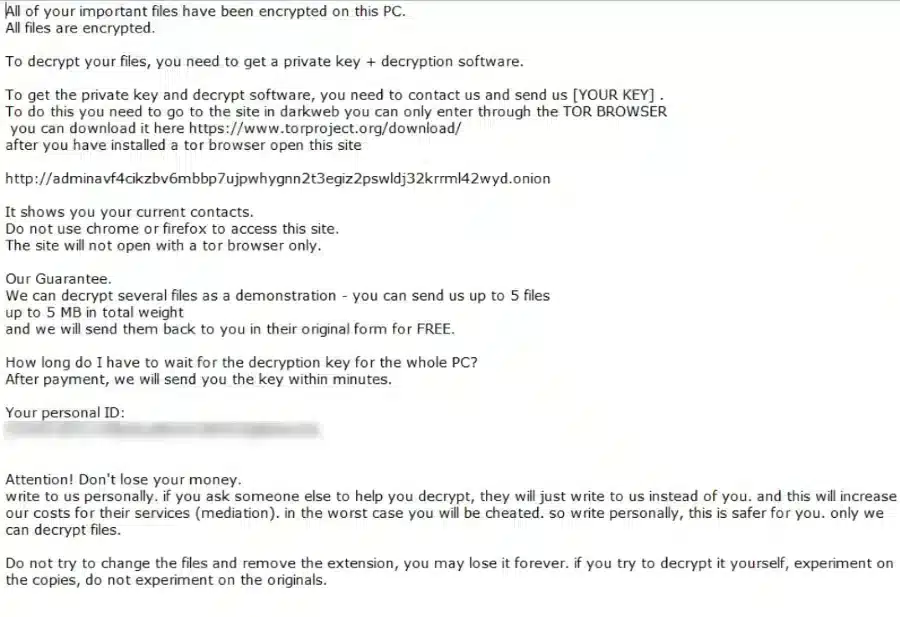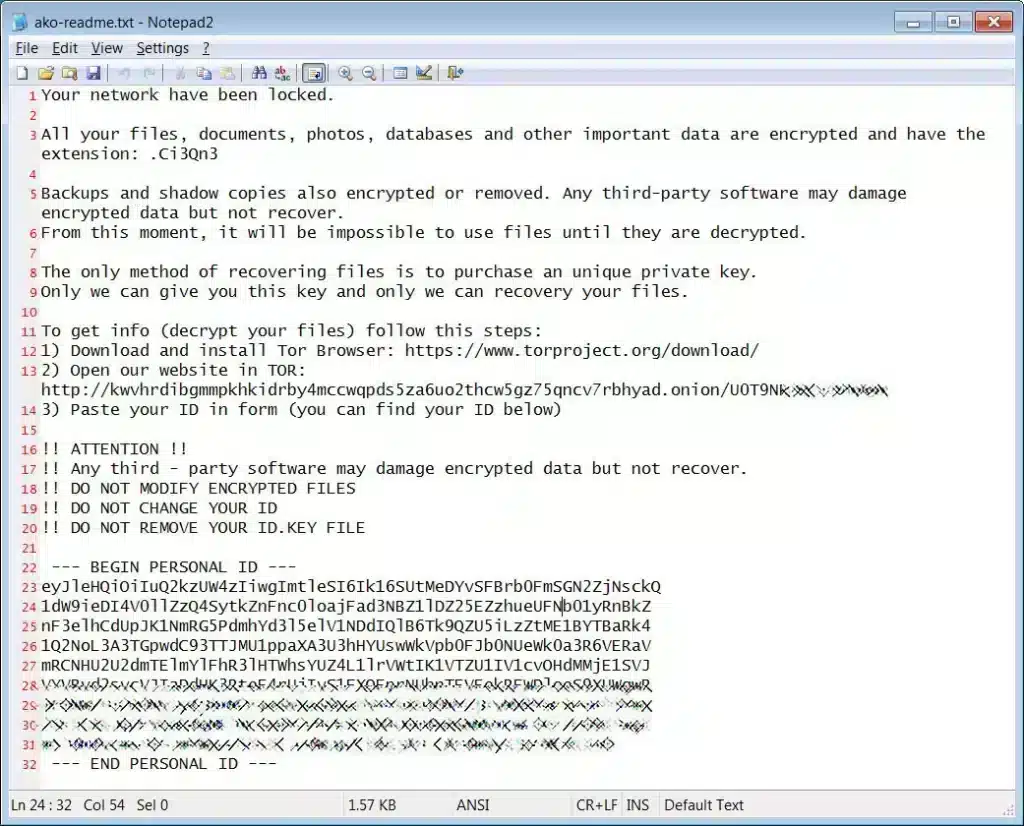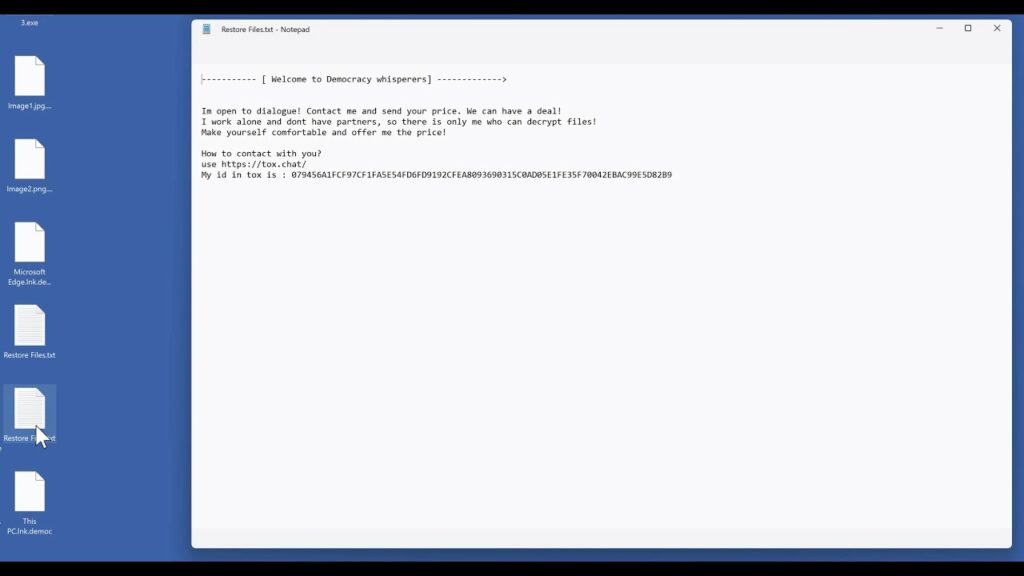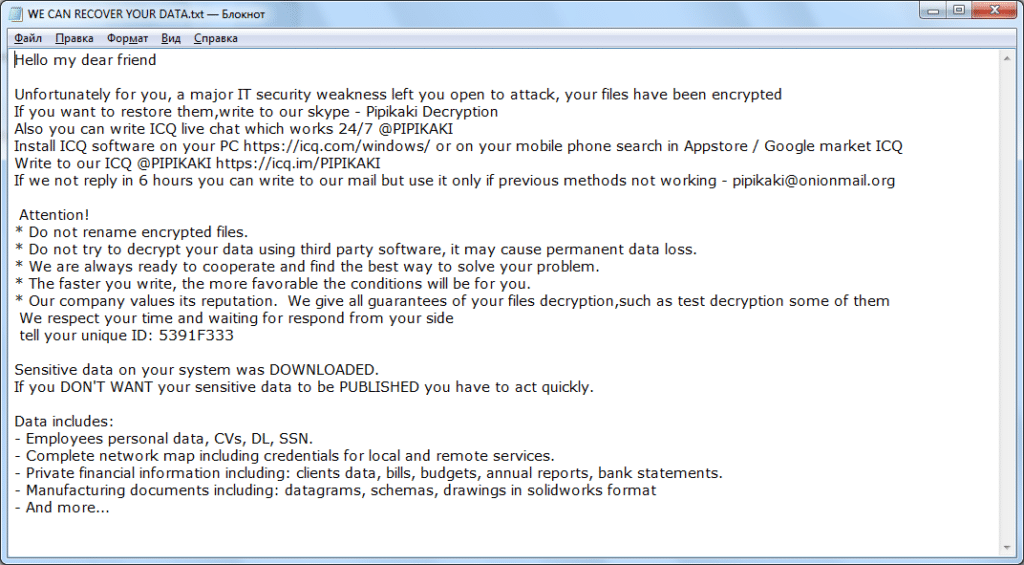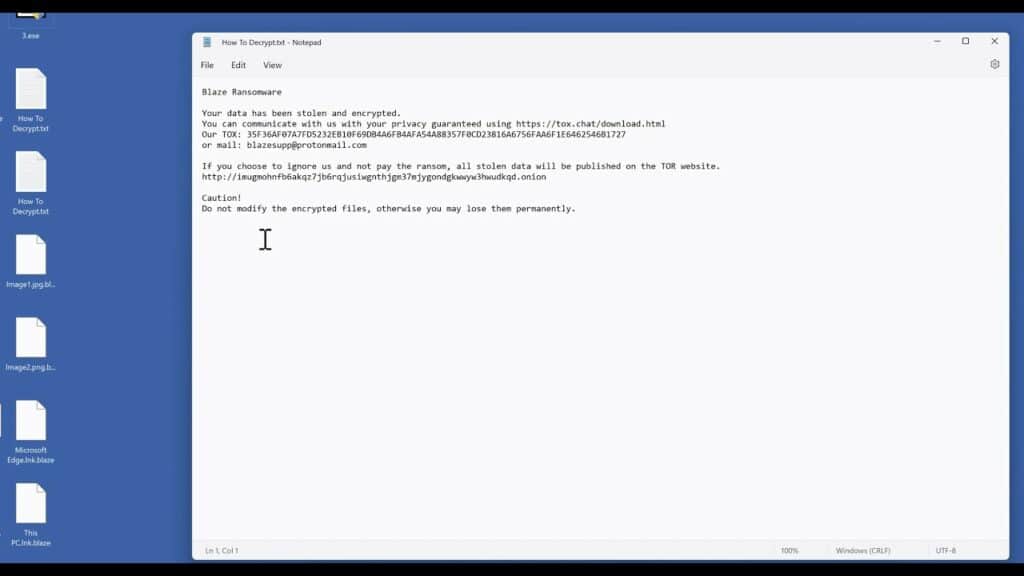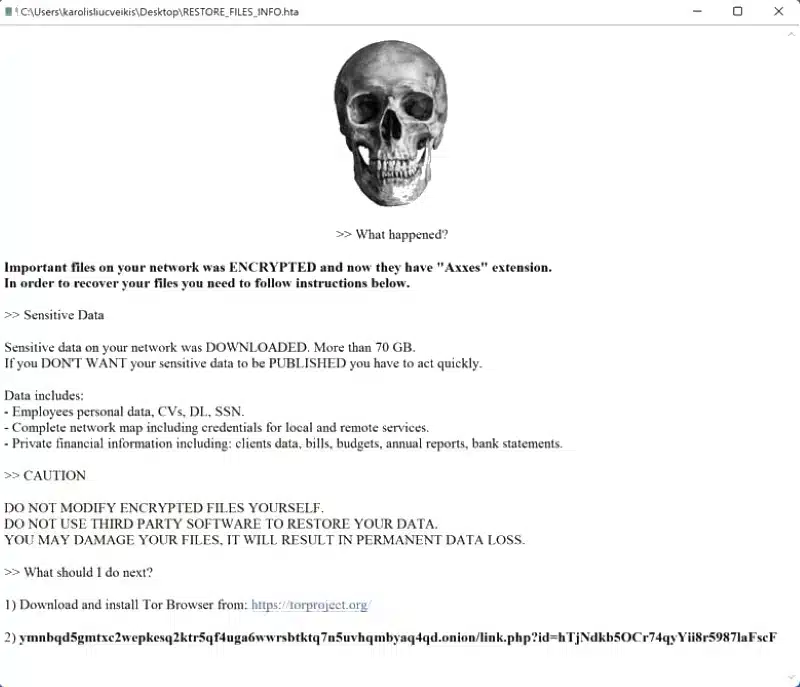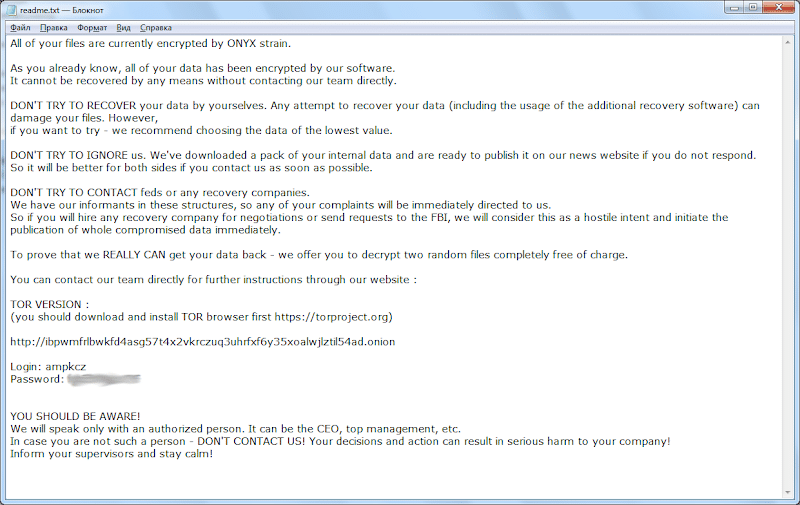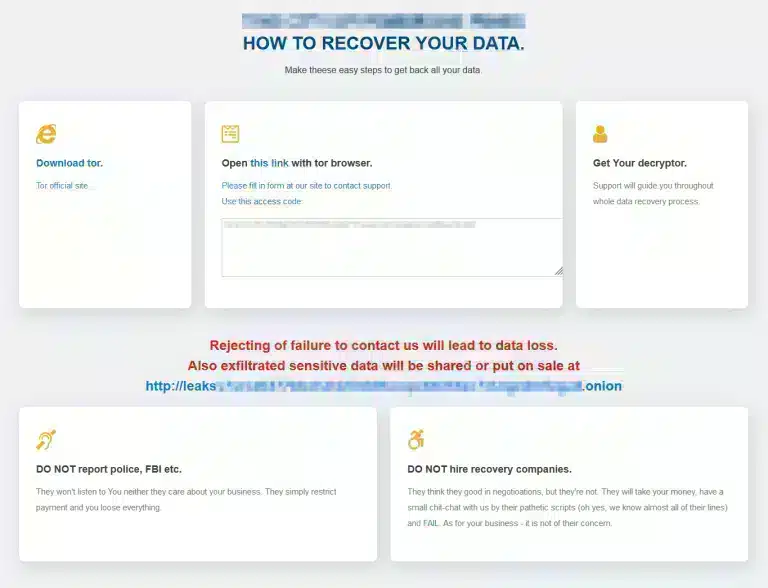
Entropy Ransomware
Entropy ransomware comes from a long line of malware that has been hacking and stealing data from large corporations for years, it is a variation of the DoppelPaymer ransomware and part of the EvilCorp gang. The gang has other ransomware such as WastedLocker, Hades and Phoenix. The EvilCorp group has become so large that the U.S. Treasury Department has placed