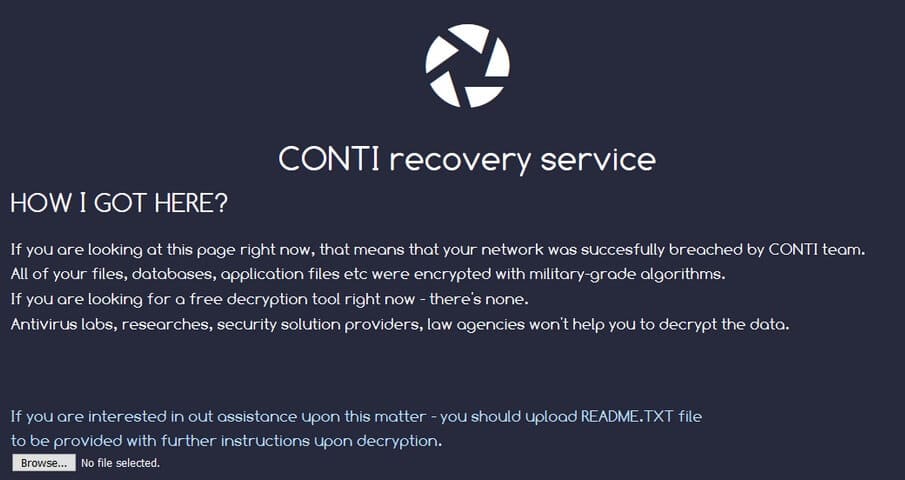
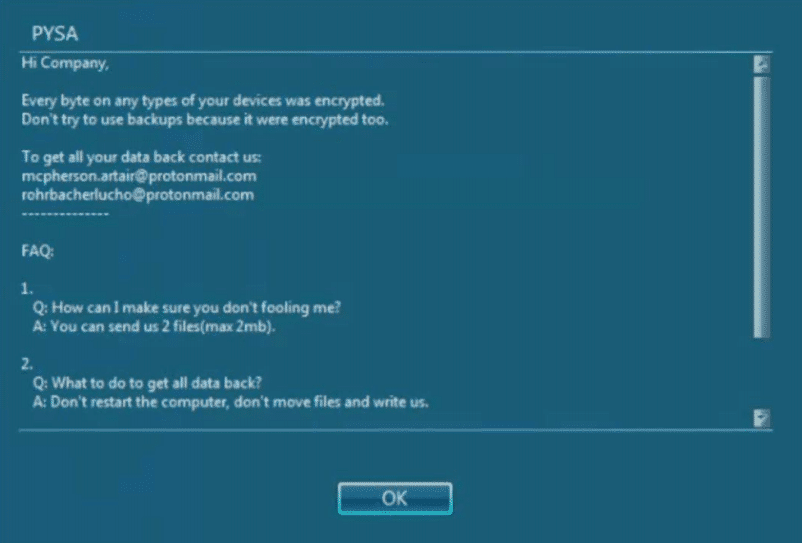
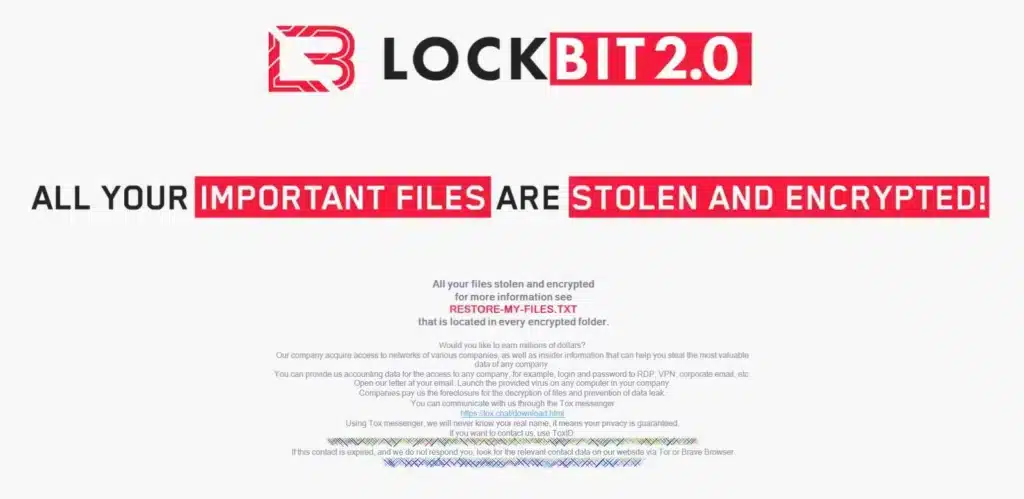
Ransomware Vice Society
The Vice Society ransomware attacks led to an update to the Windows print spooler code. The port the group used for their attacks was known as “PrintNightmare” the Windows update aimed to close this port. This flaw was in the printing system, after failing to execute the Spooler the hackers could access the operating system which granted them the same