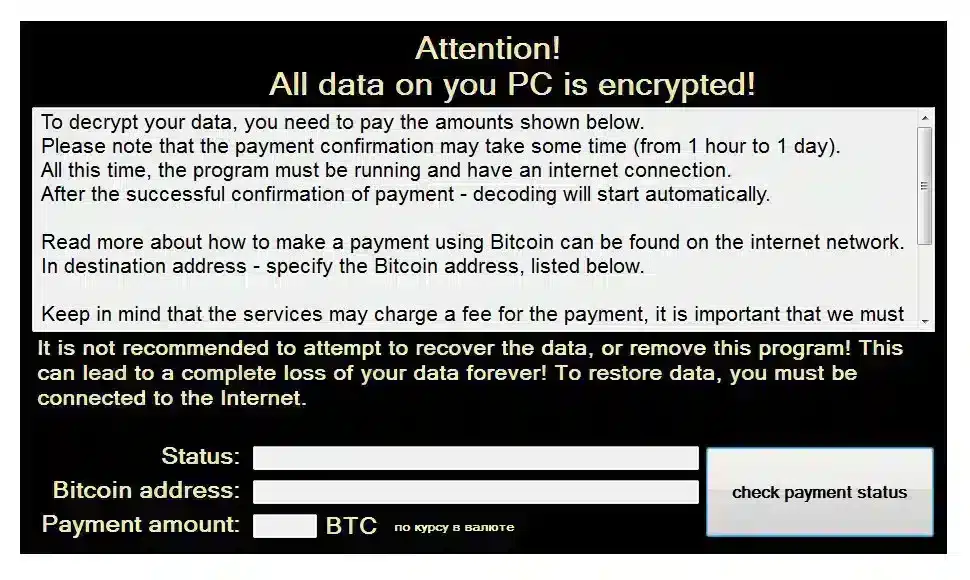
Rever Ransomware
Ransomware attacks have been on the rise these past few years, and new ransomware often emerges. This July, it was the case with Rever ransomware that has some important characteristics. The main target of Rever ransomware is Synology NAS and Windows Server systems. After breaking in, most often done via unprotected RDP or malicious emails, the attackers encrypt the files