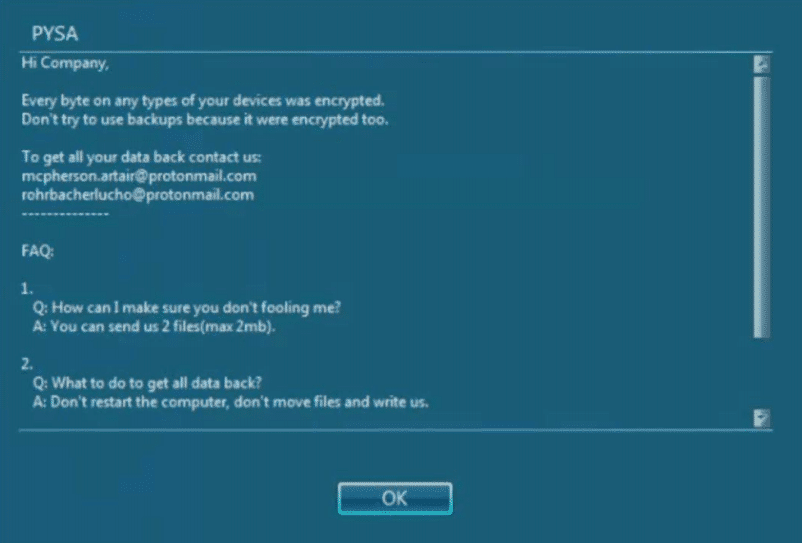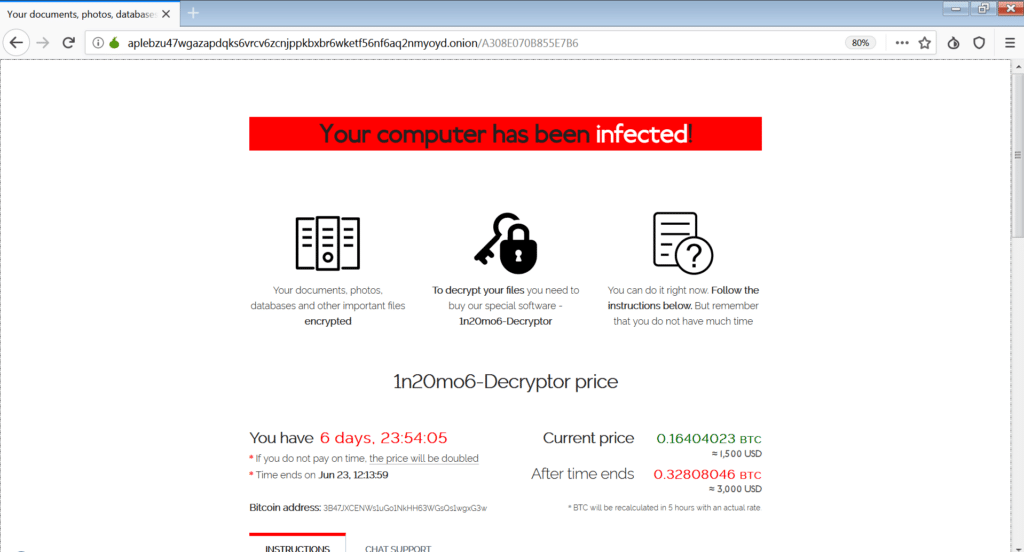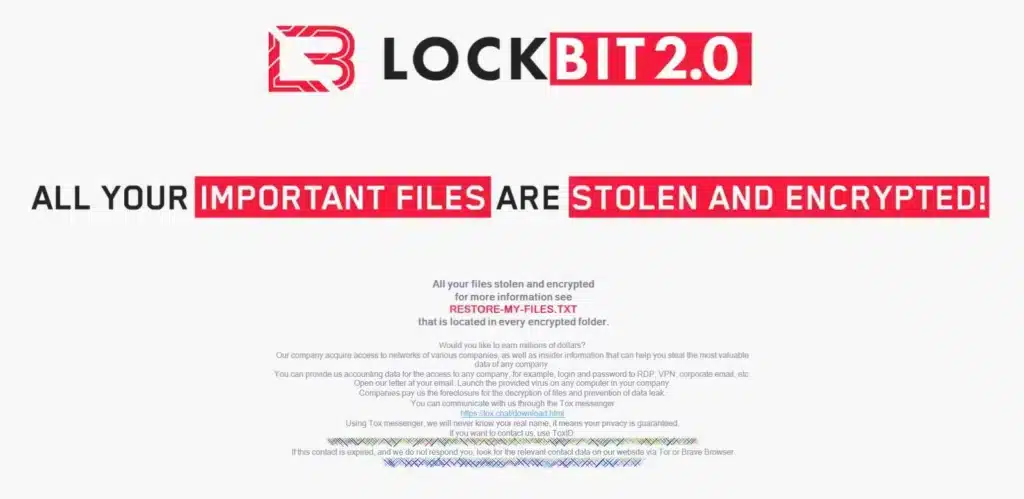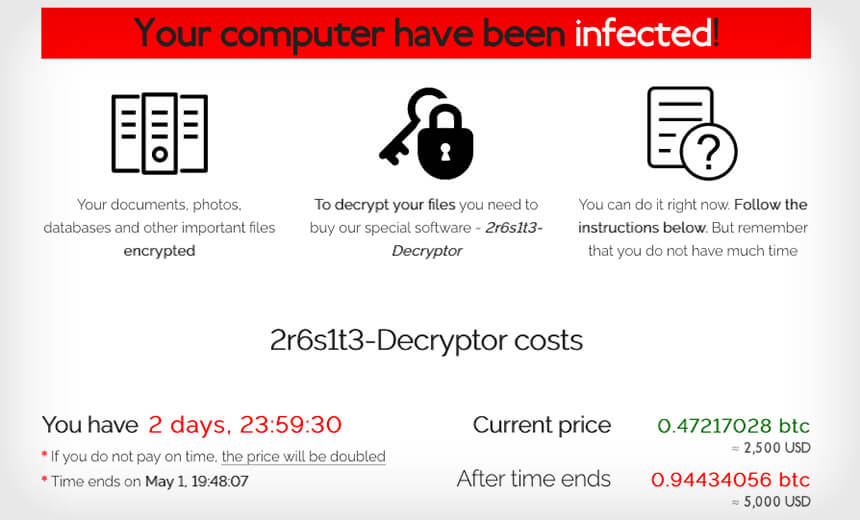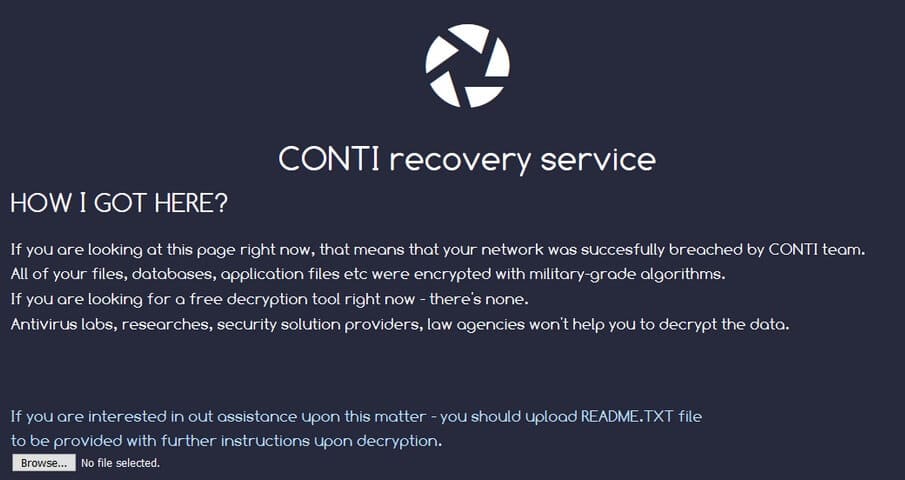
CONTI Ransomware
In May of this year, the FBI released an alert about the considerable increase in attacks carried out by the Conti Ransomware. They use the RaaS (Ransomware as a Service), which is a way of outsourcing the spread of this ransomware, amplifying the number of attacks exponentially. They are evolving this type of service, instead of paying just a commission