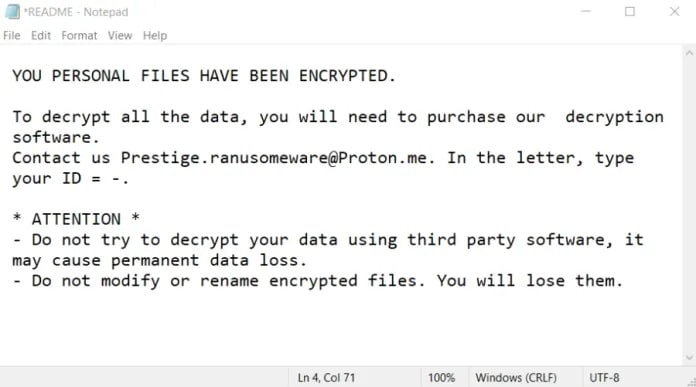
Prestige Ransomware
Prestige Ransomware is malware that encrypts files from an environment and makes them inaccessible to the user.
It has been active for the past few months and has harmed many businesses with its ransomware attacks

Prestige Ransomware is malware that encrypts files from an environment and makes them inaccessible to the user.
It has been active for the past few months and has harmed many businesses with its ransomware attacks
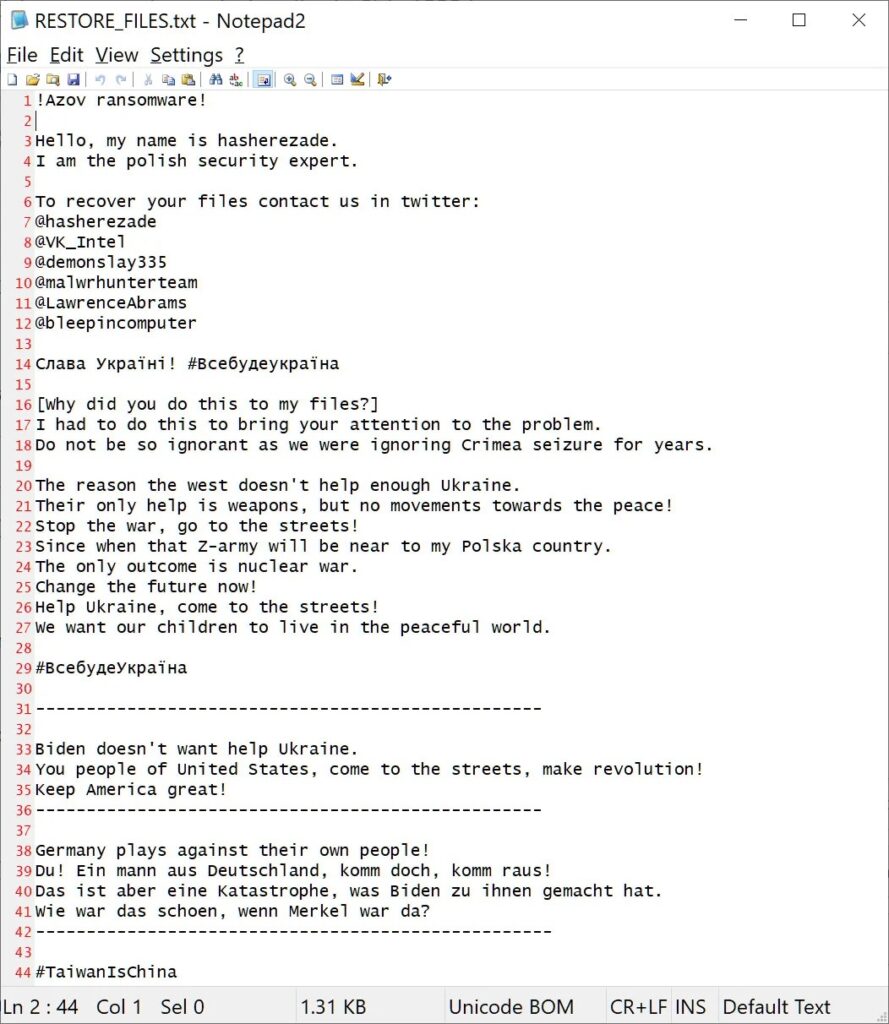
Azov Ransomware is a new destructive wiper extension that appeared in the month of October 2022. A peculiarity of this ransomware is that it is not an extortion operation as it does not charge ransoms, in fact, it only encrypts the victims’ data.
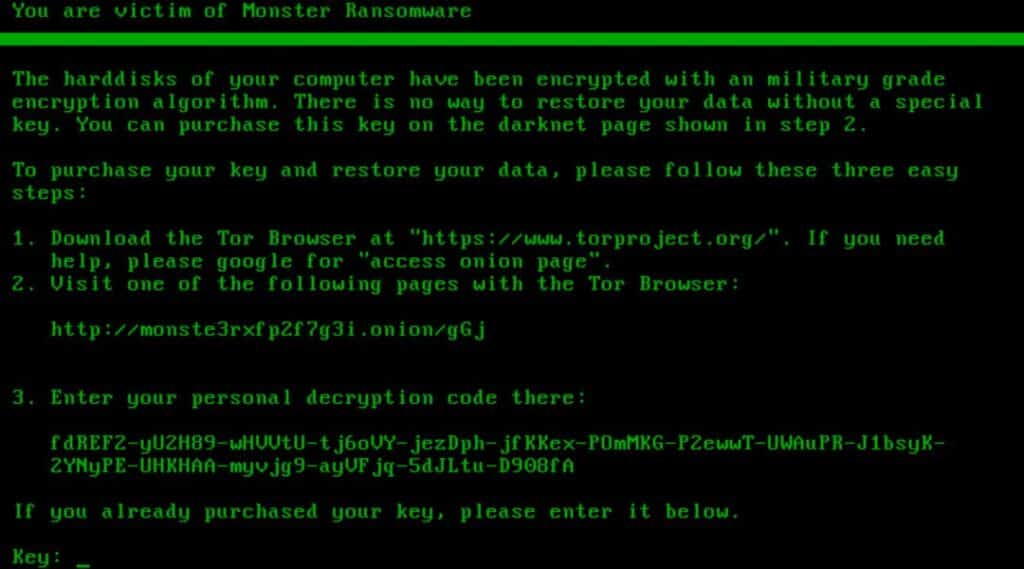
The Monster ransomware was discovered in early 2022 as they led a string of attacks targeting several companies around the world. This ransomware brought some news to the cyber world. New developments that have influenced several other ransomware after it. One of them is for sure the use of a GUI (Graphical User Interface) in its ransomware, making it more
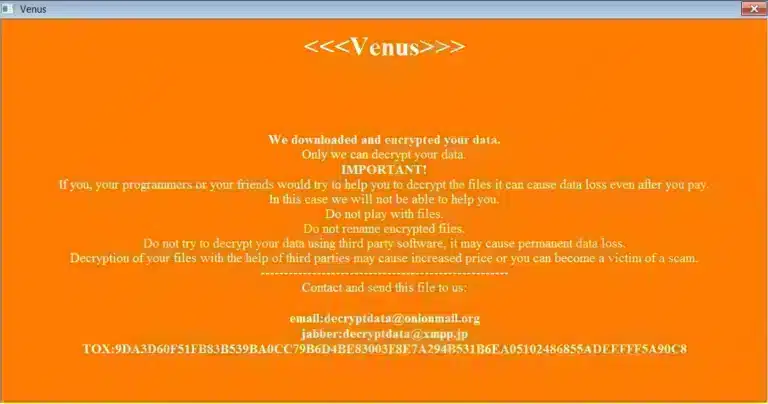
The Venus ransomware made its appearance around August 2022, and since then the group behind the ransomware has been adding names to its list of victims. Another ransomware using the same name had already appeared in 2021, but nothing other than the name shows any connection between them. The operators use Windows vulnerabilities related to the remote desktop system (RDP).
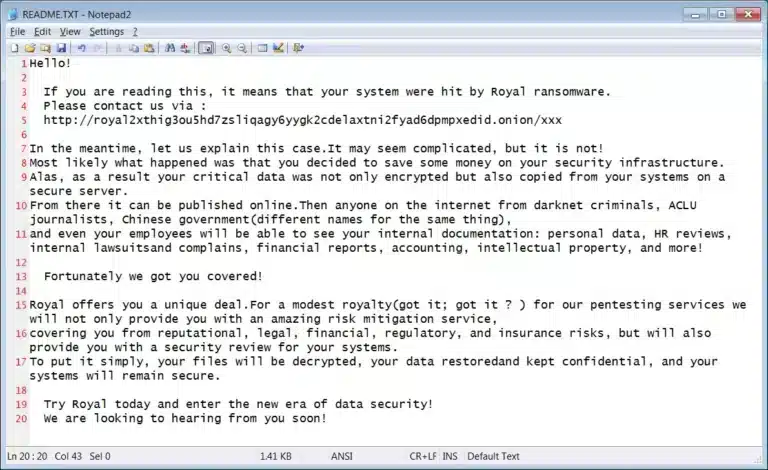
Royal is a rapidly growing ransomware operation that is targeting large companies where its ransom demands range from $250,000 to over $2 million. According to active research into the Royal group, its participants are composed of experienced operatives from other ransomware groups. For this reason, with the know-how the group has accumulated from former groups, Royal Ransomware does not operate

The VSOP ransomware appears to be directly linked to another malware that also demands ransom after stealing data from its victims. Based on the similarities in their attack processes, researchers believe VSOP may be a variant of the Onyx ransomware that was seen in May of this year. VSOP ransomware has been multiplying victims, whether they are businesses or individuals.
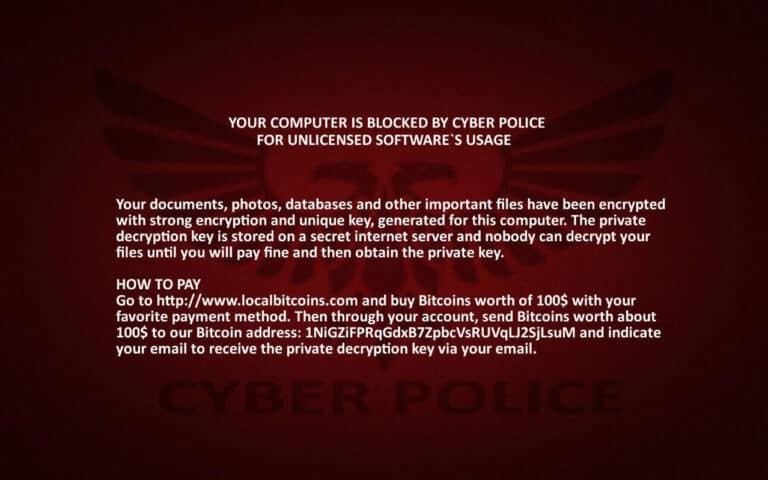
The Cyber Police ransomware has been making headway on ransomware information channels. It was discovered by Lawrence Abrams and is based on an older ransomware project called HiddenTears. Cyber Police Ransomware usually targets personal computers and servers rather than organizations. The attackers’ idea is to pose as a type of cybercrime fighting unit called “Cyber Police.” To break into the

The AgainstTheWest ransomware belongs to the hacktivist group of the same name. There is not much information yet about who the members of the group are. However, they have been carrying out attacks around the world. Among their victims today are the Chinese Ministry of Public Security and the company ByteDance, creator of the social network TikTok. With these two

The BlooDy ransomware has been known since May 2022, with an attack targeting a group of medical and dental offices in New York City. Recently, there was an event that pleased many cybercrime wannabes. After a fight between the LockBit operator and its developer, the LockBit 3.0 ransomware builder leaked on Twitter. This builder makes it accessible to anyone,
The Play ransomware began its activities in June 2022. Since then, many businesses and government institutions have fallen victim to the Play ransomware. Among them is the Judiciary of Cordoba in Argentina. A large case that involved companies such as Microsoft, Cisco and Trend Micro for the investigation into the attack. Because of the event, the IT system of the
Let's Talk?
Through unique technologies Digital Recovery can bring back encrypted data on any storage device, offering remote solutions anywhere in the world.
Discover the invisible vulnerabilities in your IT – with the 4D Pentest from Digital Recovery
This website uses cookies so that we can provide you with the best user experience possible. Cookie information is stored in your browser and performs functions such as recognising you when you return to our website and helping our team to understand which sections of the website you find most interesting and useful.
These cookies are set to provide the service, application or resource requested. Without these cookies, your request cannot be properly delivered. They are usually set to manage actions made by you, such as requesting website visual elements, pages resources or due user login/logoff. We can also use these cookies to set up essential functionalities to guarantee the security and efficiency of the service requested, like authentication and load balancer request.
If you disable this cookie, we will not be able to save your preferences. This means that every time you visit this website you will need to enable or disable cookies again.
Performance Cookies
Google Analytics is a web analytics service offered by Google that tracks and reports website traffic, currently as a platform inside the Google Marketing Platform brand.
Please enable Strictly Necessary Cookies first so that we can save your preferences!