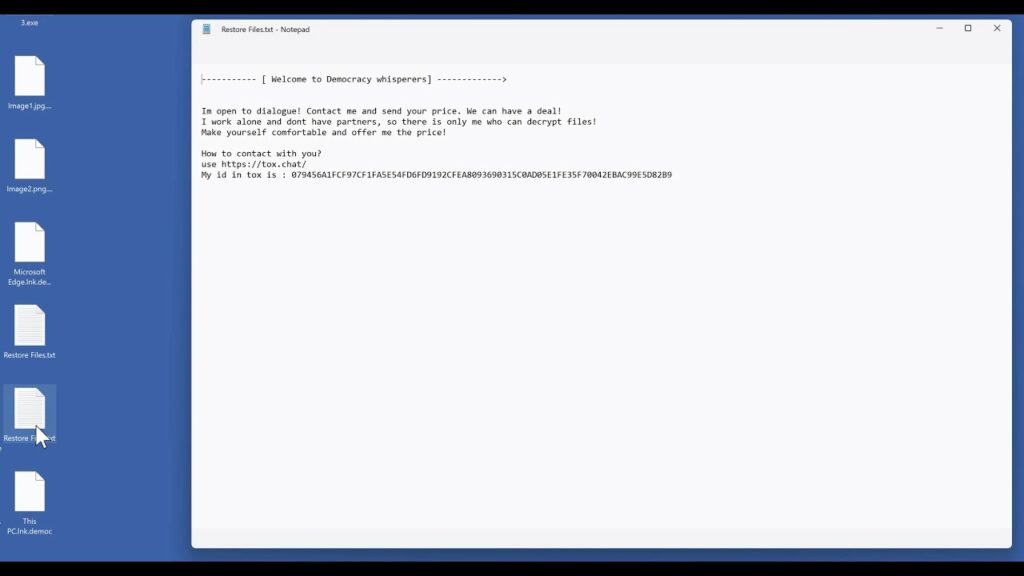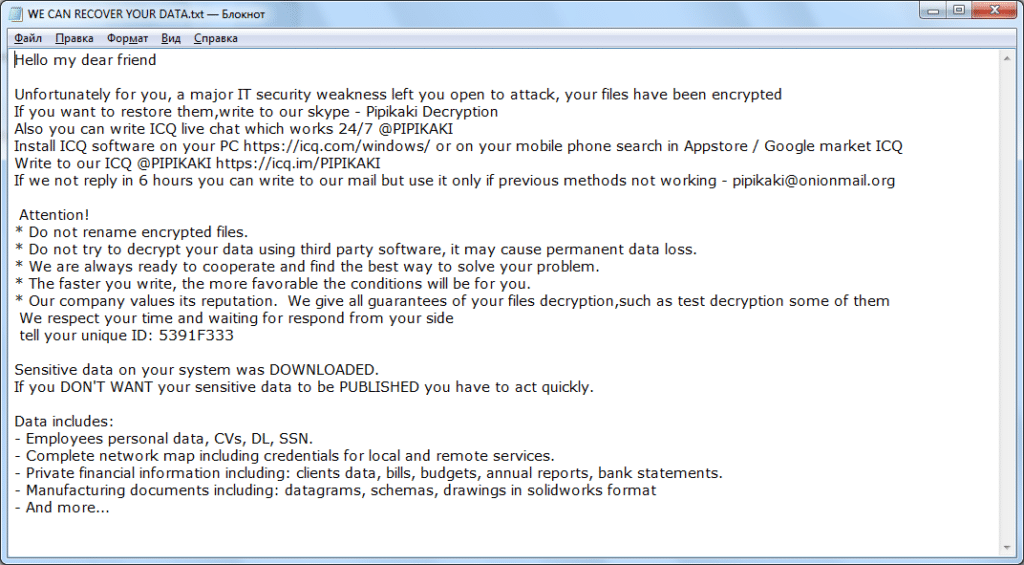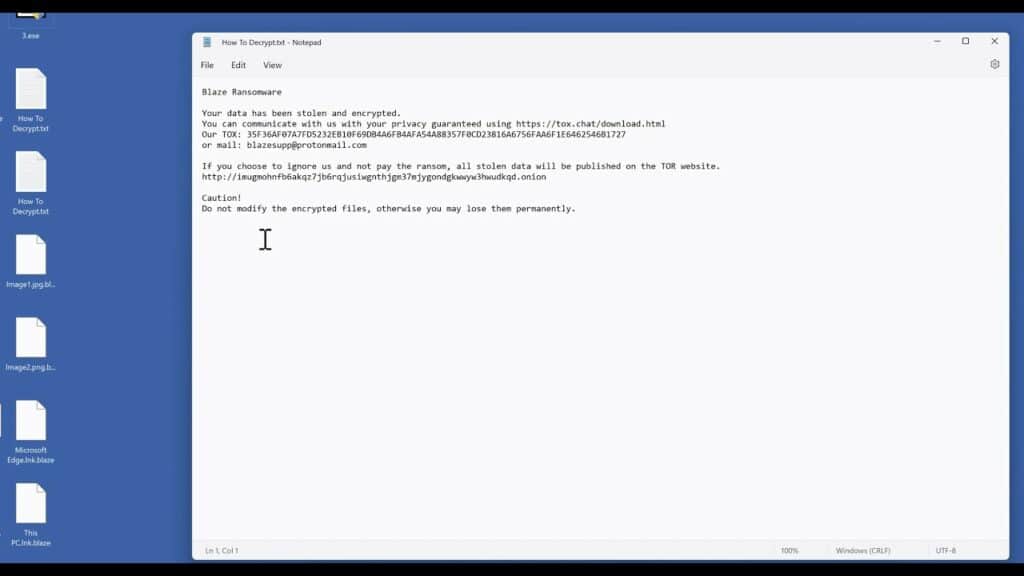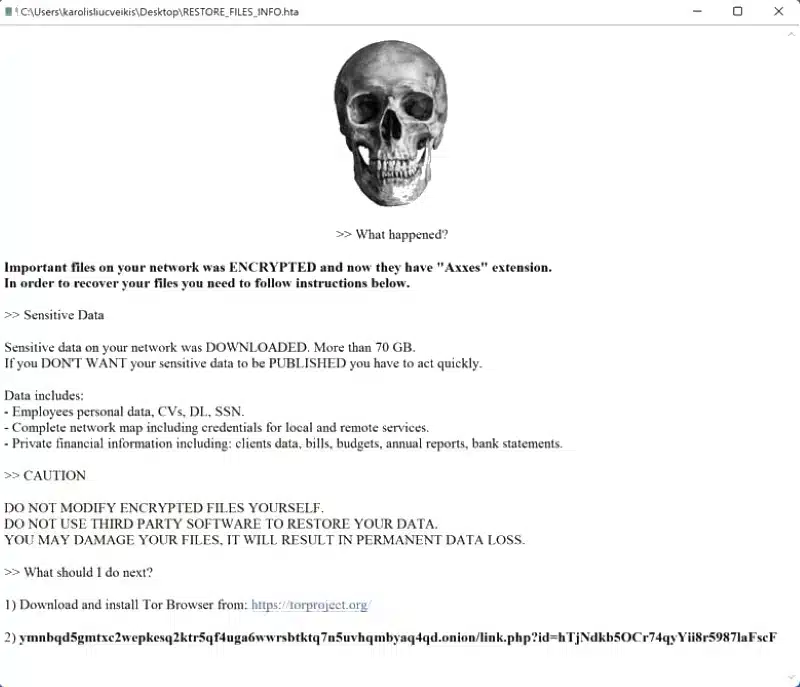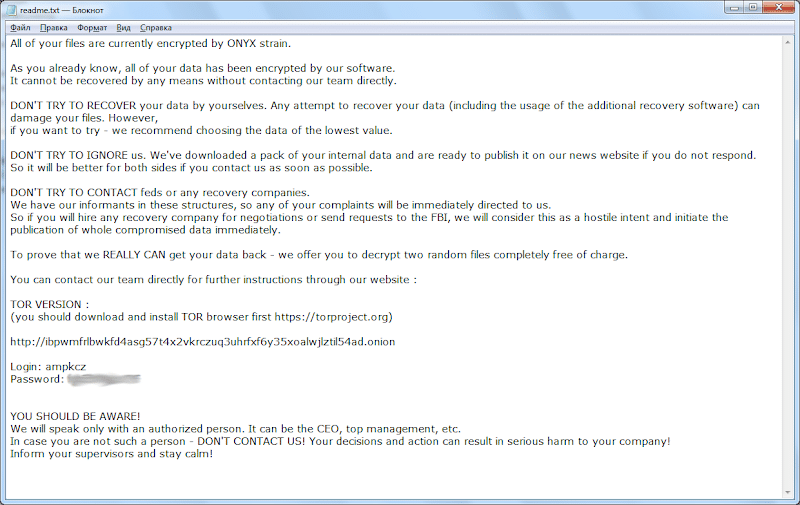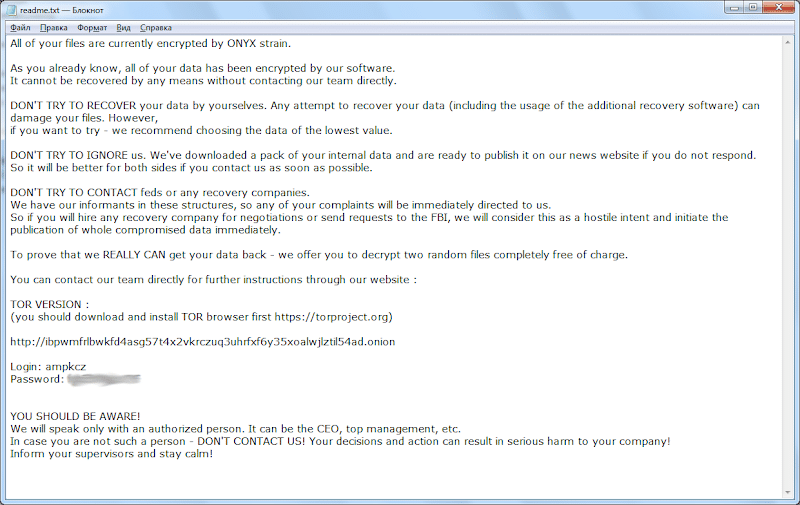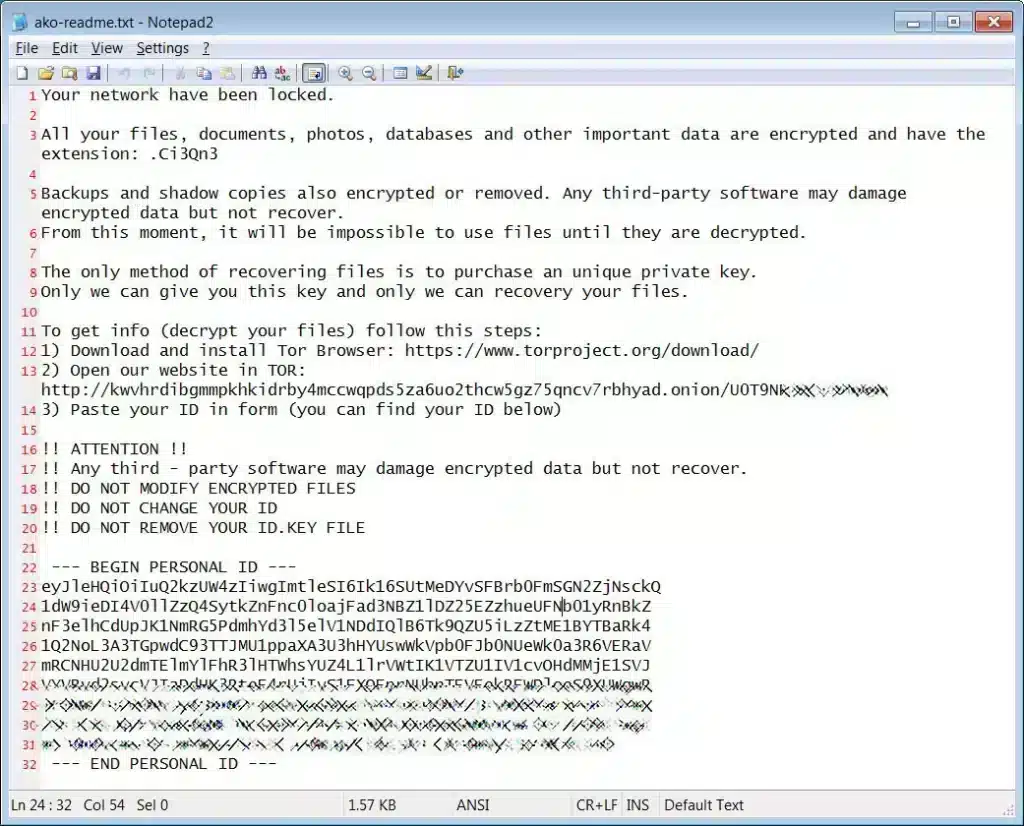
AKO Ransomware
AKO ransomware emerged in 2020, and since then a few variations have emerged, today there is an active variation responsible for numerous attacks around the world. Despite the changes and time the AKO group remains with the same tactics, double extortion remains in use. The group specialises not only in encrypting the victim’s data, but also in stealing it. After