Expert Insights
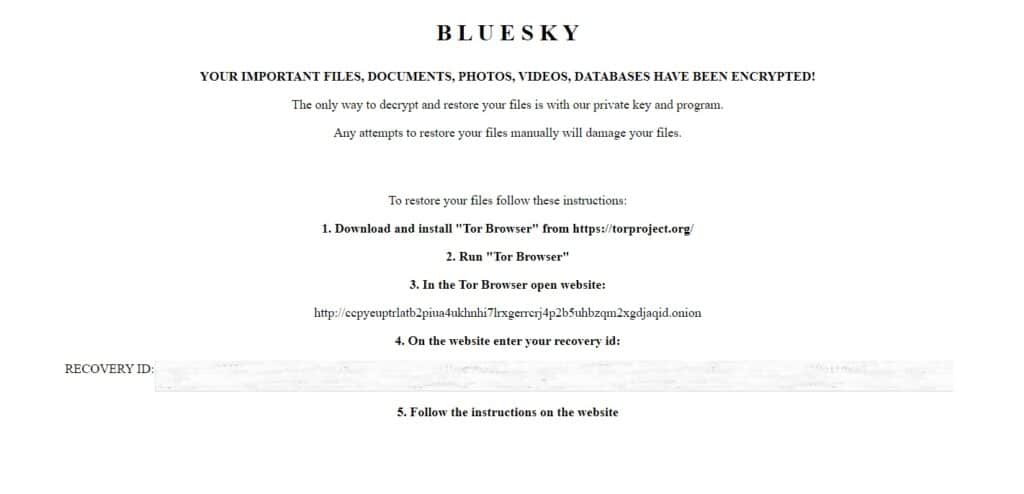
BlueSky Ransomware
BlueSky Ransomware is a new extension discovered by researchers and has many similarities to another famous group, known as Conti.
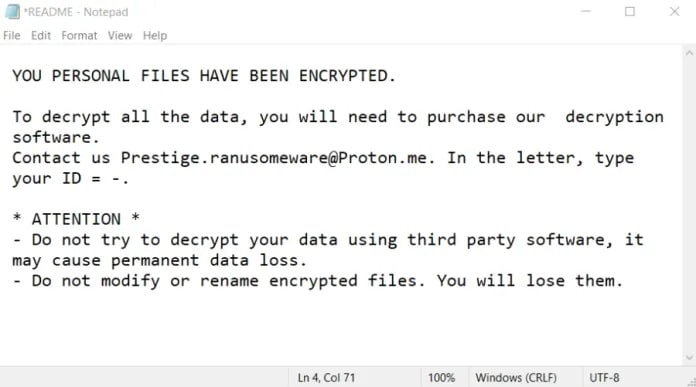
Prestige Ransomware
Prestige Ransomware is malware that encrypts files from an environment and makes them inaccessible to the user.
It has been active for the past few months and has harmed many businesses with its ransomware attacks.
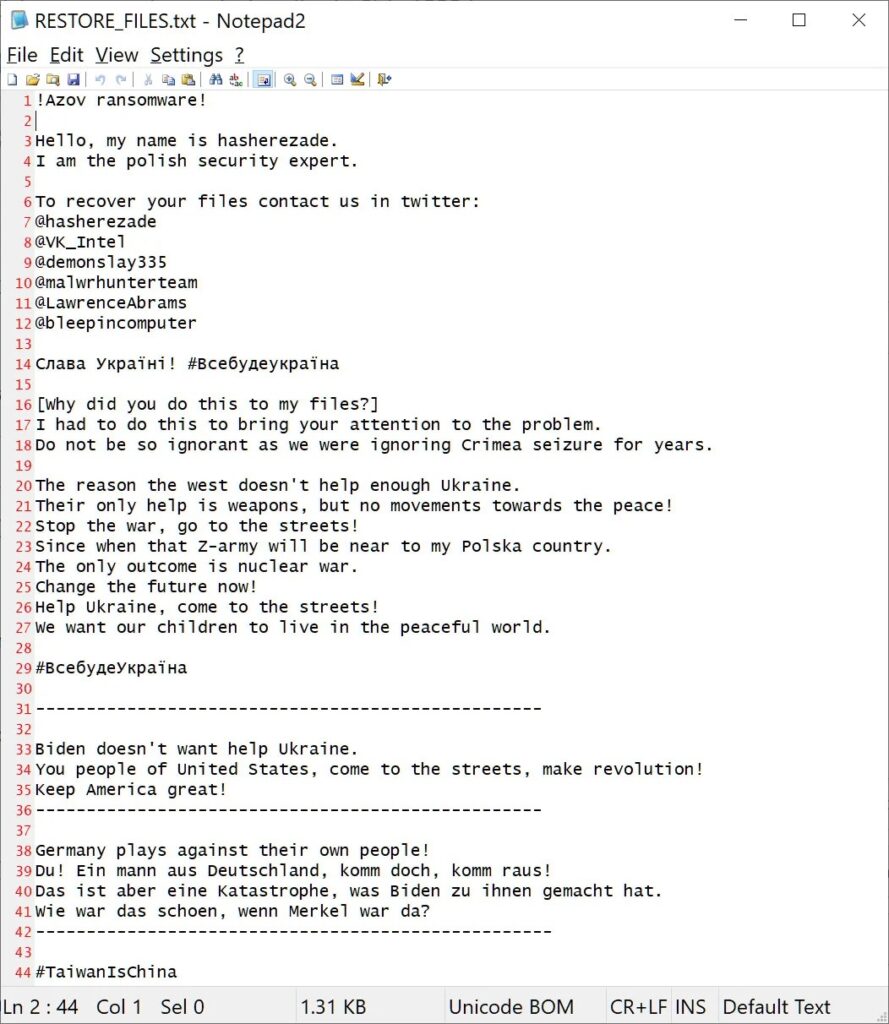
Azov Ransomware
Azov Ransomware is a new destructive wiper extension that appeared in the month of October 2022. A peculiarity of this ransomware is that it is not an extortion operation as it does not charge ransoms, in fact, it only encrypts the victims’ data.

What is Storage?
Storage is a set of hardware and software that helps you store, process and manage your data. Data storage can be used for both business and personal purposes.
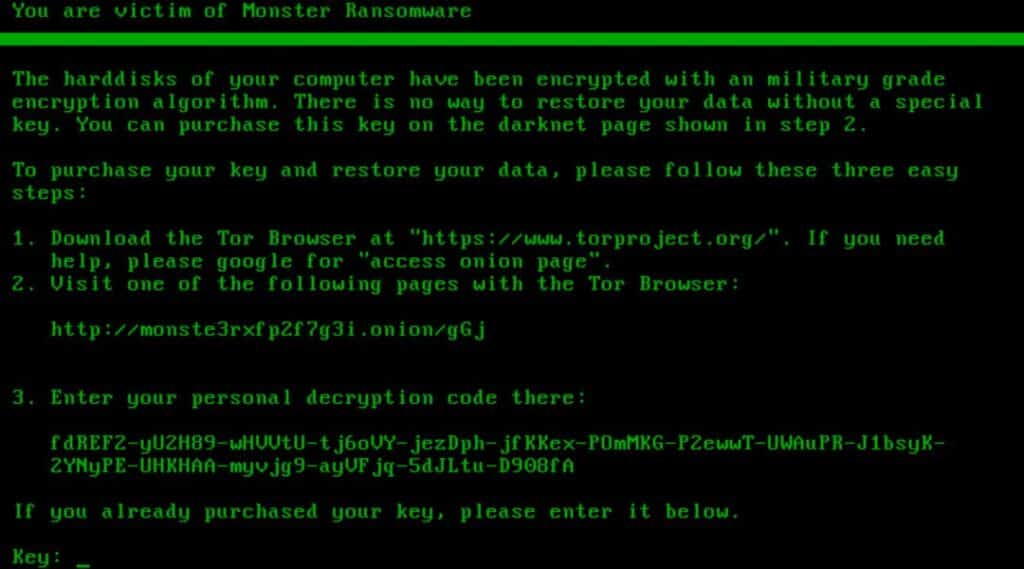
Monster Ransomware
The Monster ransomware was discovered in early 2022 as they commanded a string of attacks targeting several companies around the world. This ransomware brought some new developments to the cyber world. Novelties that influenced several other ransomware after it. One of them is certainly the use of a GUI (Graphical User Interface) in their ransomware, making it increasingly accessible for
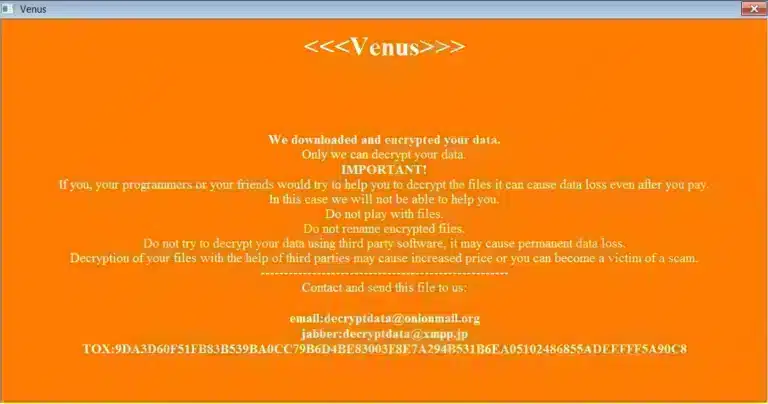
Venus Ransomware
The Venus ransomware made its appearance around August 2022, and since then the group behind the ransomware has been adding names to its list of victims. Another ransomware using the same name had already appeared in 2021, however nothing other than the name shows any connection between them. The operators use Windows vulnerabilities related to the remote desktop system (RDP).
