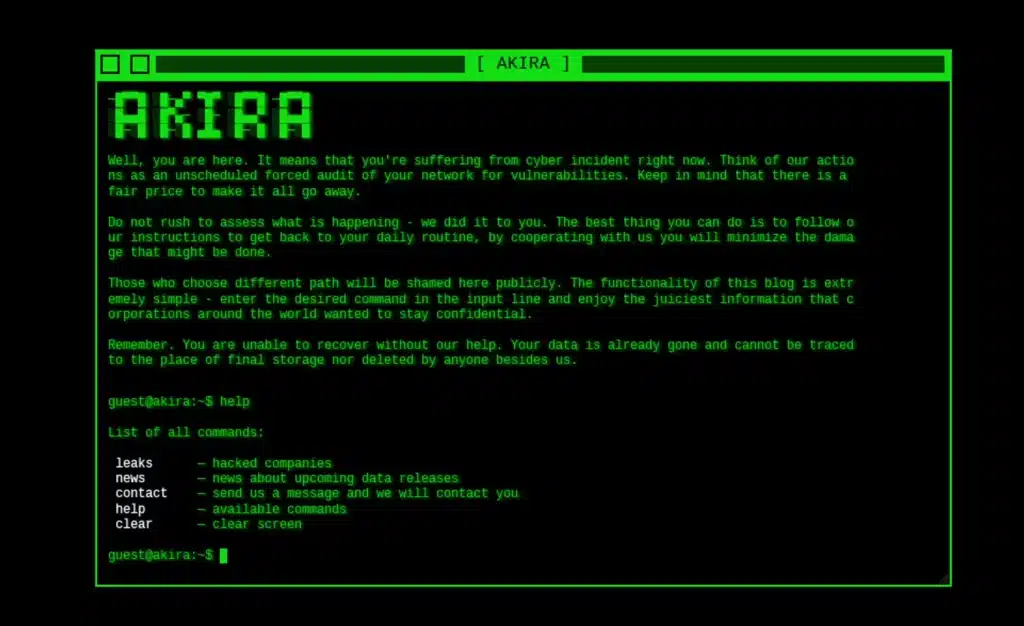
Recovering Microsoft Access is possible with our solutions
Data security is a primary concern in any digital environment, and Microsoft Access, as a widely used database management tool, is not immune to cyber threats. One of the most damaging forms of attack is ransomware, a type of malware that encrypts a system’s data and demands a ransom to restore access. When Microsoft Access is compromised by ransomware, the